SecurStar ShareCrypt 6 - User Manual
Document Changes
| Date | Author | Change |
|---|---|---|
| 02/01/2019 | J Cowlishaw | First Outline |
| 04/01/2019 | J Cowlishaw | Fleshed out installation & First Use. Added screenshots |
| 07/01/2019 | J Cowlishaw | Added: Workflows, Login, Logout, Encryption Areas, Multiple Users, Adding Users and Troubleshooting |
Index
Overview
ShareCrypt stores files encrypted on local disk, network shared folders, and file syncing cloud services. It provides user based access rights to folders and thier content.
Storing files in cloud sync or backup services can leave data vulnerable toaccess from unauthorized people. Data may be subject to rogue staff, court orders or law enformcement requests. Common services such as Dropbox, Google Drive and Microsoft SkyDrive do not provide data security from these issues; data may be encrypted in transit or at rest, but using cryptographic keys in possession of the service.
With sharecrypt you have full control of your senstive data ensuring that only you can access your data and locking out any unauthorized party (including hosting company).
ShareCrypt enables you to separate data and restrict access; Finance dept can prevent IT dept from accessing thier files, HR can prevent Finance from accessing employee data, yet IT can ensure data is backed up and verified. Even with these precautions, specific users may be granted access to some or all areas.
ShareCrypt is easy to use, it provides a virtual disk drive, under which all areas to which the user has access are visible. Files are encrypted individually with AES 256 bit keys, which are hashed with the user’s password using SHA 256. New user requests are encrypted with 2048 bit RSA public-private keys.
ShareCrypt is entirely peer-to-peer. A client user generates a new area (with it’s own AES 256bit encryption key) and invites or grants users access to the area. Where access to the area has been granted, the area key is shared with the new user and hashed with the new users password. Read, Write and Admin permissions can be set on a per user, per area basis. Every user granted access to an area can use the files in the normal manner for a shared folder.
The only thing an administrator has to do is to make an empty shared disk/folder available for read/write access over the network (could be local network or interent drive).
System administrators may handle the encrypted files and manage data backup in the normal fashion, without access to file content.
ShareCrypt does not require any software installation on the fileserver. This way, all CIFS/SMB server systems like MS Windows, Novell Netware 6 and UNIX with Samba are supported.
ShareCrypt is fully scalable and allows the creation and management of an unlimited amount of encrypted disks/folders. (The size of encrypted disks is also unlimited)
Installation
Download and run the installer from http://securstar.com/ShareCrypt5/download ShareCrypt 5 has no server component, so install it on each client machine from which access will be required.
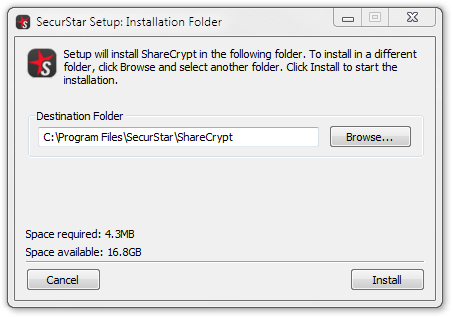
After successful installation, ShareCrypt will be started for initial configuration.
Each time ShareCrypt is started, you will see the Demo mode warning. Visit http://securstar.com/purchase.php to purchase a license. While in demo mode, Sharecrypt will present this window and encryption keys will be protected by a less

First use & Configuration
After a successful installation, ShareCrypt will execute and walk you through the process of creating your first area and user.

Configure:
- Destination Folder - where encrypted data is to be stored, local or on a network share)
- Drive Letter - the disk through which decrypted files are available)
- Area Name - See Encryption Areas
Click OK to elevate and allow these settings to be written (these apply to all instances of ShareCrypt 5 on the client machine).
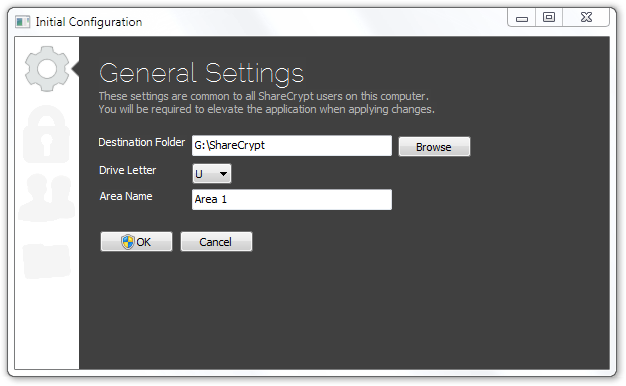
Enter your new credentials (username & password) to access all areas you are to be assigned to.
After entering credentials, you will be notified if the configuration has been successful.
The login window will now be visible. (see below)
Workflows
Login
Now login with your new credentials.

The encrypted material will be available under the previously configured disk drive (Drive U: in the example below). You will see it is marked as a Removable Drive, and it’s capacity is reported as that of the disk which hosts the Destination Folder (G: here).

Note: You can also access the ShareCrypt drive by double clicking on the ShareCrypt Taskbar Icon (this may be hidden by Windows 7 by default).
Logout
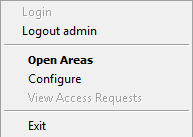
To prevent access to the ShareCrypt contents, you can Log Out. Right click on the Tasktray icon and select Logout [username].
Encryption Areas
Multiple areas can be created (See Adding Areas), each with it’s own set of assigned users. You may want to create an area for each team (Finance, Support, Directors etc). Contents of the Finance area cannot be accessed by users of the Support area, unless the user is assigned to both.
Adding Areas
The fourth section of the Configure page allows you to view, open and create Encryption Areas.
Enter the name for a new area ‘Area Name’ and your current password, with which to encrypt the area credentials.
A new area will be created in the Destination Folder and available in the Sharecrypt Drive.
Restrictions on using Areas
There is no user interface for removing areas.

Multiple Users
A user consists of a set of credentials. While the initial installed client generates the first user, more can be added at any time.
A user may be assigned to any number of Areas, each with differing levels of access (Read, Write and Admin).
Adding Users
A new user may be in two ways, described below. The first requires an Admin user to review requests after they are made by the new user.
On Demand
Execute ShareCrypt 5, Supply a user name and check the ‘New User?’ option on the Login Screen. The user will be guided to select which Areas for which access should be requested, and to enter a password with which to access the granted Areas.
Once requested, a User with Admin rights for the Area(s) must confirm the access. After this, the user will be able to login and see the Area(s) assigned and the contained data.
Pre-Authorized
A User with Admin rights for an area may pre-authorize specific new users for that area. This means that the user follows the On Demand instructions, except no further interaction is required from an Admin user.
The third section of the Configure page allows you to view & modify user access to Areas. Additionally, an Admin user may create a pre-authorized invite for a new user to specific areas.
Click the ‘Invite New User’ button and select the access rights the named user should be allowed. Specify a user name (and optionally a Windows user name to which the invite is restricted).

Disabling User Access
A user may have rights revoked by an Admin of the area in question. Ensure a user has Read, Write and Admin fields cleared before applying changes. This will prevent the user from being able to decrypt data contained in the specific area, but not prevent the user from signing in to ShareCrypt 5.
Troubleshooting
No ShareCrypt drive visible in ‘Computer’
Note: INSTALL_DIR refers to the ShareCrypt 5 installation folder. For example:
C:\Program Files\SecurStar\ShareCrypt
or
C:\Program Files(x86)\SecurStar\ShareCrypt
Check the following conditions:
- INSTALL_DIR\ShareCrypt.exe is running
- INSTALL_DIR\mounter.exe is running as the DokanMounter service
- The drive letter is not currently assigned to some other device. Check the registry value ‘DriveLetter’ in the key ‘HKEY_LOCAL_MACHINE\SOFTWARE\SecurStar\ShareCrypt5’ and modify if necessary.
New user cannot access an Area
A new user may not be given access if the Admin user(s) responsible for the area have not logged in since an On Demand request was made.
Files in ShareCrypt drive root folder
No files may be placed in the root of the drive. Only Area folders will appear on the drive.
Deleting Areas
Some of the files critical to maintain user access to an area are protected from inadvertant deletion in Windows Explorer.
.Acl.AK files can be deleted from a commandline by using a wildcard character (*). Once these are removed, Windows Explorer can be used to remove the entire folder structure from the Destination Folder (see First use & Configuration)
Credits
ShareCrypt is built on several opensource technologies. Licenses can be found in the installation directory.